BULK IDENTITY THEFT
Identity theft is one of the most common and damaging forms of hack. For both innovative online brands and established “brick and clicks” brand names with a significant online business, protection of customer credentials is paramount. From financial institutions providing on-line account access, to on-line retailing and gaming, store and loyalty cards and multiple other scenarios, there is a long list of companies who need to store, manage and transact with sensitive customer data.
Typically web servers are hacked over the internet, and credentials are stolen from databases and other password stores. Hackers know its easier and faster to steal passwords at rest from a single location than it is to infect large numbers of client computers or capture credentials in transit. It can take less than a minute to steal a million passwords.
Stolen identities are routinely advertised on the dark web for $1 to $5 per record. Credentials originating from banks are advertised for $7 or more per record. With many customers re-using passwords across multiple websites and services, password theft compromises not only your service but others as well. That’s why password repositories are a honeypot for hackers.
TIME TO STEAL ONE MILLION PASSWORDS
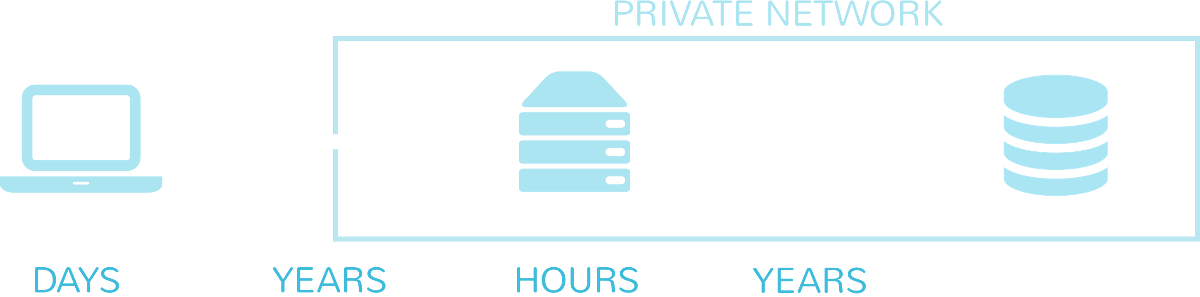
It takes years to capture and decipher one million active passwords in transit, days to capture them from clients or web servers, and only seconds to steal them from a password repository database. This is why the database is a favourite target for hackers.
INEFFECTIVE COUNTERMEASURES
Existing countermeasures such as hashing and salting passwords can mitigate against theft. But the development of techniques such as hash chains and rainbow tables, combined with the availability of cheap computer processing power, has severely degraded the protection of these techniques.
Strong encryption does not prevent identity theft, it just makes it much harder to de-cipher data after it has been stolen. Theft of encrypted data still triggers an expensive and disruptive remediation process. Regulatory bodies need to be informed, customers must be warned and passwords have to be changed as a precaution.
Two-factor and multi-factor alternatives to passwords enhance identification of the customer and make impersonation harder at the client end. However passwords still need to be stored securely at the business end.
THE COSTS OF RECOVERY
There have been numerous high profile bulk password thefts in recent years. Loss of identity data results in huge inconvenience to both companies and their customers, and there are significant financial implications for breached organisations.
Remediation costs can include but are not limited to:
- Significant reputational damage, loss of customer trust and brand erosion
- Financial losses stemming from disruption to trading
- Costs associated with cleaning up, restoring or rebuilding affected systems
- Regulatory sanctions such as the new European Commission GDPR Directive with up to 2% of turnover levied in fines
- Possible compensation claims, threat of litigation or class action
According to the Verizon 2020 Data Breach Investigation Report “Credential theft, social attacks (i.e., phishing and business email compromise) and errors cause the majority of breaches (67% or more)”
The 2019 Cost Of Data Breach Report conducted by Ponemon for IBM, estimates the average total cost of a data breach is now US $3.9m. The average cost per record, which might be a username and password combination, is US $150 per record.
A STANDARD ARCHITECTURE
The IT industry uses the same industry standard architecture, otherwise known as the PC, for everything. It provides economies of scale with an inexpensive solution to most problems, but also common vulnerabilities across all classes of products, including supposedly secure products. The fundamentals of this architecture are:
- A processor vulnerable to Malware attack: a PC executing the common x86 instruction set is both high performing and highly vulnerable to code injection attacks, infecting a computer with malicious programs posing as data.
- A software platform too big to trust: operating systems and applications software such as web servers and databases comprise millions of lines of code requiring a vast software code base for security.
- Permissions-based security: Administrators are afforded special access to manage identities. But if a permissions escalation attack is successful or the administrator password is stolen then security is instantly breached.
This architecture currently has tens of thousands of known security vulnerabilities, and more are discovered daily. According to cyber-security firm McAfee Inc, there are currently 130 million malicious programs available to steal identity information. Can you afford to take the risk that your company will be the next target?